EENews reports on the increase in physical threats to the US power grid in the past couple of years in Tensions at home and abroad pose growing threat to US grid
Rising incidents of domestic terrorism and a surge in state-sponsored cyber attacks on critical infrastructure are posing a heightened risk to the U.S. power system, the nation’s grid reliability authority warned last week.
The geopolitical turmoil from the Israeli-Hamas conflict and the ongoing Russian-Ukrainian war is driving a dramatic increase in malicious cyber activity, according to the North American Electric Reliability Corp., a nonprofit body in charge of setting reliability standards for the wholesale power system. Those international tensions are adding to the steady increase in domestic physical threats against the power infrastructure that are likely to climb as the U.S. election season ramps up.
“The current geopolitical situation has significant ramifications for the North American grid,” Manny Cancel, senior vice president at NERC, told reporters Thursday, and that’s contributed to “a dramatic increase in malicious cyber activity.”
Cancel, who is also CEO of NERC’s Electricity Information Sharing and Analysis Center, which gathers and analyzes data from power companies, said at the same time, U.S.-based threats could include a wide range of activities aimed at shutting off the power for large swaths of people to sow unrest.
“We know activists continue to use this as a vehicle to get their ideology and other political thoughts across,” said Cancel. “So nonetheless, we’re going to be very vigilant during this current election cycle.”
Physical threats against the grid have seen a sharp uptick in recent years, according to a POLITICO analysis of DOE data. The nation’s power providers reported 185 instances of mostly physical attacks or threats against critical grid infrastructure in 2023, beating the previous record number of reports from 2022 and doubling the number of incidents in 2021.
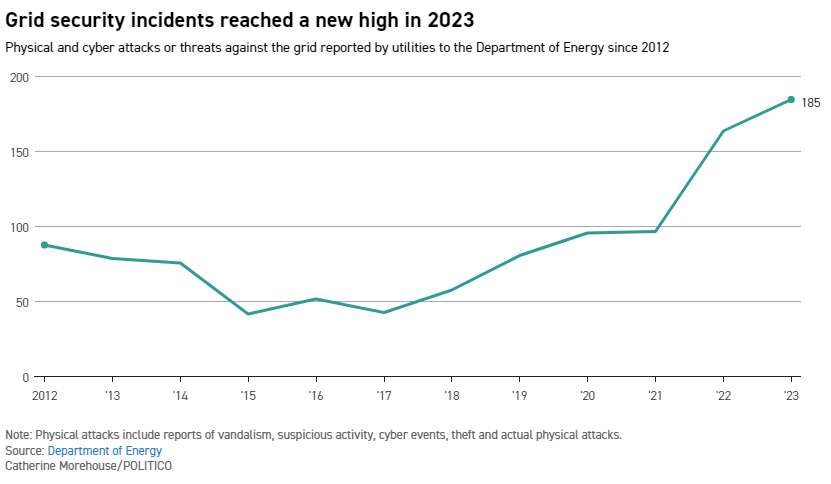
Security experts say that rise correlates to the growth in domestic extremism and terrorism, fueled by public messaging boards and rampant information sharing that offers a guide for people to target weak spots in the power system.
“There is ample publicly available information for bad actors to identify vulnerable assets and choke points that, if taken offline, could have significant sustained consequences for this system,” Victor Atkins, a former associate deputy director for operations under the Department of Energy’s Office of Intelligence and Counterintelligence.
Utilities reported more than 2,800 physical security threats to the center in 2023, according to Cancel, a jump of more than 1,000 from the previous year.
NERC spokesperson Rachel Sherrard said the increase “can be largely attributed to enhancements in members’ information sharing.” She added the increased number of incidents “is not necessarily indicative of an increase in risk.”
Cancel said the vast majority of physical threats and attacks don’t result in power outages — only about three percent have any impact on the grid.
None of the recent incidents have led to the kind of cascading outages or widespread failures on the scale of the notorious Northeast blackout of 2003, which shut down the power system from Michigan to Massachusetts and as far as Northern Ontario.
But localized impacts from these incidents can still be devastating.
A shooting attack in 2022 against two North Carolina substations left 45,000 people without power for four days. The state’s medical examiner has blamed the attack for the death of an 87-year-old woman whose oxygen machine failed.
California utilities avoided a crisis last week after an unknown suspect attempted to destroy a local substation by shooting at a transformer and shutting off circuit breakers. The FBI is offering a $25,000 reward for information on the suspected shooter. An FBI official told a local news station that if the attack had succeeded, it could have led to catastrophic consequences for people relying on electricity for medical purposes.
Brian Leventhal, a spokesperson for the impacted utility Southern California Edison, said SCE “uses a multilayered, defense in-depth strategy at our facilities to deter and respond to security threats.”
Cyber threats have also been on the rise, but are more difficult to directly quantify, according to Cancel.
DOE’s data include only a handful of suspected cyber attacks. But the NERC center has recorded a rise in the number of security weaknesses in the power system. From 2023 to 2022, the National Institute of Science and Technology recorded a jump of about 2,000 system vulnerabilities — a pace of about 60 additional threats per day, Cancel said.
What’s clear to U.S. officials is that hackers linked to U.S. adversaries are plenty capable of wreaking havoc on the power system.
“The major nation state actors — China, North Korea, Iran and Russia — absolutely possess the capability to disrupt critical infrastructure here in North America,” said Cancel.
“When they’ll decide to use this is obviously a very complicated decision. But nonetheless, we accept the fact that they have the capability,” he added.
Several high profile cyber breaches have proved those nations’ capabilities.
Last year, the Department of Energy was among federal and state agencies impacted by a mass cyberattack through vulnerable software. And a vulnerability revealed late last year — now dubbed “CitrixBleed” — launched warnings from federal security agencies who found state-backed hackers were exploiting the vulnerability to access major U.S. companies.
A POLITICO investigation from last year found reporting gaps between federal and state officials, as well as grid and security authorities, related to ongoing threats against the grid.
Atkins, who is now a consultant focused on reducing risks to critical infrastructure, warned the U.S. power grid vulnerabilities were due to the “patchwork” of federal and local, public and private entities involved in maintaining security of the grid. He described it as a “paradigm of diffused responsibility.”
“It seems to me that it is only a matter of time before the sophistication and coordination of these attack scenarios reach a point to cause much more catastrophic consequences,” he said.



















